Merge remote-tracking branch 'upstream/master'
This commit is contained in:
commit
12a7f0af44
|
|
@ -28,7 +28,12 @@ broadcasted UDP frame that includes the CSI information:
|
|||
nexutil -m1
|
||||
tcpdump -i wlan0 -xxx
|
||||
```
|
||||
Soon, we will publish a MATLAB script to analyze those raw CSI dumps.
|
||||
To analyze the dumped CSI information, we provide some MATLAB functions in the
|
||||
`matlab` directory. They rely on reading dumped CSI information from pcap files
|
||||
created using tcpdump. As an example, we provide the captures created for our
|
||||
MobiSys 2018 paper. The result looks as follows:
|
||||
|
||||
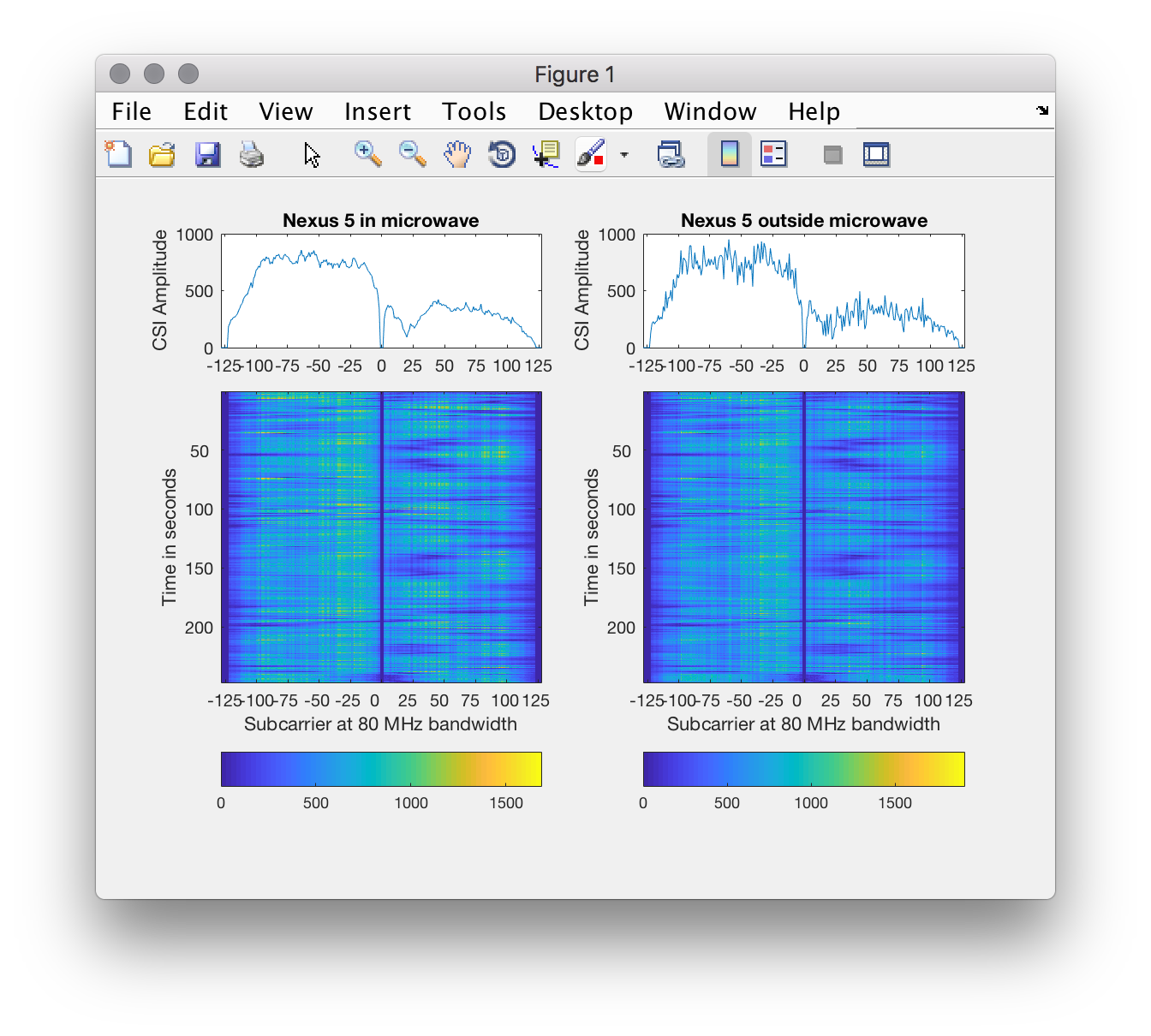
|
||||
|
||||
# Extract from our License
|
||||
|
||||
|
|
|
|||
|
|
@ -0,0 +1,102 @@
|
|||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
% %
|
||||
% ########### ########### ########## ########## %
|
||||
% ############ ############ ############ ############ %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ########### #### ###### ## ## ## ## ###### %
|
||||
% ########### #### # ## ## ## ## # # %
|
||||
% ## ## ###### ## ## ## ## # # %
|
||||
% ## ## # ## ## ## ## # # %
|
||||
% ############ ##### ###### ## ## ## ##### ###### %
|
||||
% ########### ########### ## ## ## ########## %
|
||||
% %
|
||||
% S E C U R E M O B I L E N E T W O R K I N G %
|
||||
% %
|
||||
% License: %
|
||||
% %
|
||||
% Copyright (c) 2018 Jakob Link, Matthias Schulz %
|
||||
% %
|
||||
% Permission is hereby granted, free of charge, to any person obtaining a %
|
||||
% copy of this software and associated documentation files (the %
|
||||
% "Software"), to deal in the Software without restriction, including %
|
||||
% without limitation the rights to use, copy, modify, merge, publish, %
|
||||
% distribute, sublicense, and/or sell copies of the Software, and to %
|
||||
% permit persons to whom the Software is furnished to do so, subject to %
|
||||
% the following conditions: %
|
||||
% %
|
||||
% 1. The above copyright notice and this permission notice shall be %
|
||||
% include in all copies or substantial portions of the Software. %
|
||||
% %
|
||||
% 2. Any use of the Software which results in an academic publication or %
|
||||
% other publication which includes a bibliography must include %
|
||||
% citations to the nexmon project a) and the paper cited under b) or %
|
||||
% the thesis cited under c): %
|
||||
% %
|
||||
% a) "Matthias Schulz, Daniel Wegemer and Matthias Hollick. Nexmon: %
|
||||
% The C-based Firmware Patching Framework. https://nexmon.org" %
|
||||
% %
|
||||
% b) "Matthias Schulz, Jakob Link, Francesco Gringoli, and Matthias %
|
||||
% Hollick. Shadow Wi-Fi: Teaching Smartphones to Transmit Raw %
|
||||
% Signals and to Extract Channel State Information to Implement %
|
||||
% Practical Covert Channels over Wi-Fi. Accepted to appear in %
|
||||
% Proceedings of the 16th ACM International Conference on Mobile %
|
||||
% Systems, Applications, and Services (MobiSys 2018), June 2018." %
|
||||
% %
|
||||
% c) "Matthias Schulz. Teaching Your Wireless Card New Tricks: %
|
||||
% Smartphone Performance and Security Enhancements through Wi-Fi %
|
||||
% Firmware Modifications. Dr.-Ing. thesis, Technische Universität %
|
||||
% Darmstadt, Germany, February 2018." %
|
||||
% %
|
||||
% 3. The Software is not used by, in cooperation with, or on behalf of %
|
||||
% any armed forces, intelligence agencies, reconnaissance agencies, %
|
||||
% defense agencies, offense agencies or any supplier, contractor, or %
|
||||
% research associated. %
|
||||
% %
|
||||
% THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS %
|
||||
% OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF %
|
||||
% MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. %
|
||||
% IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY %
|
||||
% CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, %
|
||||
% TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE %
|
||||
% SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. %
|
||||
% %
|
||||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
|
||||
function csi_plot(csi_buff_microwave, csi_buff_outside)
|
||||
xticks = [4:25:254];
|
||||
|
||||
subplot(4,2,1)
|
||||
plot(-128:127, abs(csi_buff_microwave(1,:)))
|
||||
xlim([-128 127])
|
||||
set(gca,'xtick',xticks - 129);
|
||||
title('Nexus 5 in microwave')
|
||||
ylabel('CSI Amplitude')
|
||||
|
||||
subplot(4,2,2)
|
||||
plot(-128:127, abs(csi_buff_outside(1,:)))
|
||||
xlim([-128 127])
|
||||
set(gca,'xtick',xticks - 129);
|
||||
title('Nexus 5 outside microwave')
|
||||
ylabel('CSI Amplitude')
|
||||
|
||||
subplot(4,2,[3 5 7])
|
||||
imagesc(abs(csi_buff_microwave))
|
||||
set(gca,'xtick',xticks);
|
||||
set(gca,'xticklabel',xticks - 129);
|
||||
set(gca,'ytick',0:500:2500);
|
||||
set(gca,'yticklabel',(0:500:2500)/10);
|
||||
colorbar('southoutside')
|
||||
xlabel('Subcarrier at 80 MHz bandwidth')
|
||||
ylabel('Time in seconds')
|
||||
|
||||
subplot(4,2,[4 6 8])
|
||||
imagesc(abs(csi_buff_outside))
|
||||
set(gca,'xtick',xticks);
|
||||
set(gca,'xticklabel',xticks - 129);
|
||||
set(gca,'ytick',0:500:2500);
|
||||
set(gca,'yticklabel',(0:500:2500)/10);
|
||||
colorbar('southoutside')
|
||||
xlabel('Subcarrier at 80 MHz bandwidth')
|
||||
ylabel('Time in seconds')
|
||||
end
|
||||
Binary file not shown.
Binary file not shown.
|
|
@ -0,0 +1,217 @@
|
|||
%READCSI Extract and interpret CSI values.
|
||||
% READCSI(BASE_FILENAME, SHOULD_SAVE, SHOULD_PLOT) opens the
|
||||
% BASE_FILENAME.pcap to extract channel state information (CSI) dumped
|
||||
% using nexmon's CSI Extractor firmware patch. If SHOULD_SAVE is 1,
|
||||
% extracted values will be written to BASE_FILENAME.mat. If SHOULD_PLOT
|
||||
% is 1, then CSI values will directly be plotted.
|
||||
%
|
||||
% Payload format:
|
||||
% 14 byte: Ethernet header
|
||||
% 20 byte: IPv4 header
|
||||
% 8 byte: UDP header
|
||||
% 4 byte: Magic String "CSIS"(0x43 0x53 0x49 0x53)
|
||||
% 6 byte: HW address
|
||||
% 4 byte: reserved
|
||||
% 1020 byte: 255 CSI value pairs
|
||||
%
|
||||
% CSI value pair format:
|
||||
% 2 byte: two's complement real
|
||||
% 2 byte: two's complement imag
|
||||
%
|
||||
|
||||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
% %
|
||||
% ########### ########### ########## ########## %
|
||||
% ############ ############ ############ ############ %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ########### #### ###### ## ## ## ## ###### %
|
||||
% ########### #### # ## ## ## ## # # %
|
||||
% ## ## ###### ## ## ## ## # # %
|
||||
% ## ## # ## ## ## ## # # %
|
||||
% ############ ##### ###### ## ## ## ##### ###### %
|
||||
% ########### ########### ## ## ## ########## %
|
||||
% %
|
||||
% S E C U R E M O B I L E N E T W O R K I N G %
|
||||
% %
|
||||
% License: %
|
||||
% %
|
||||
% Copyright (c) 2018 Jakob Link, Matthias Schulz %
|
||||
% %
|
||||
% Permission is hereby granted, free of charge, to any person obtaining a %
|
||||
% copy of this software and associated documentation files (the %
|
||||
% "Software"), to deal in the Software without restriction, including %
|
||||
% without limitation the rights to use, copy, modify, merge, publish, %
|
||||
% distribute, sublicense, and/or sell copies of the Software, and to %
|
||||
% permit persons to whom the Software is furnished to do so, subject to %
|
||||
% the following conditions: %
|
||||
% %
|
||||
% 1. The above copyright notice and this permission notice shall be %
|
||||
% include in all copies or substantial portions of the Software. %
|
||||
% %
|
||||
% 2. Any use of the Software which results in an academic publication or %
|
||||
% other publication which includes a bibliography must include %
|
||||
% citations to the nexmon project a) and the paper cited under b) or %
|
||||
% the thesis cited under c): %
|
||||
% %
|
||||
% a) "Matthias Schulz, Daniel Wegemer and Matthias Hollick. Nexmon: %
|
||||
% The C-based Firmware Patching Framework. https://nexmon.org" %
|
||||
% %
|
||||
% b) "Matthias Schulz, Jakob Link, Francesco Gringoli, and Matthias %
|
||||
% Hollick. Shadow Wi-Fi: Teaching Smartphones to Transmit Raw %
|
||||
% Signals and to Extract Channel State Information to Implement %
|
||||
% Practical Covert Channels over Wi-Fi. Accepted to appear in %
|
||||
% Proceedings of the 16th ACM International Conference on Mobile %
|
||||
% Systems, Applications, and Services (MobiSys 2018), June 2018." %
|
||||
% %
|
||||
% c) "Matthias Schulz. Teaching Your Wireless Card New Tricks: %
|
||||
% Smartphone Performance and Security Enhancements through Wi-Fi %
|
||||
% Firmware Modifications. Dr.-Ing. thesis, Technische Universität %
|
||||
% Darmstadt, Germany, February 2018." %
|
||||
% %
|
||||
% 3. The Software is not used by, in cooperation with, or on behalf of %
|
||||
% any armed forces, intelligence agencies, reconnaissance agencies, %
|
||||
% defense agencies, offense agencies or any supplier, contractor, or %
|
||||
% research associated. %
|
||||
% %
|
||||
% THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS %
|
||||
% OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF %
|
||||
% MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. %
|
||||
% IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY %
|
||||
% CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, %
|
||||
% TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE %
|
||||
% SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. %
|
||||
% %
|
||||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
|
||||
function csi_buff = readcsi(base_filename, should_save, should_plot)
|
||||
|
||||
%% parameters
|
||||
% configure WLAN object and get parameters
|
||||
cfgVHT = wlanVHTConfig; % legacy mode
|
||||
%cfgVHT.Modulation = 'OFDM'; % OFDM
|
||||
cfgVHT.ChannelBandwidth = 'CBW80'; % 20MHz
|
||||
cfgVHT.MCS = 0; % BPSK 6Mbps
|
||||
cfgVHT.NumTransmitAntennas = 1; % one antenna
|
||||
|
||||
FFTLength = helperFFTLength(cfgVHT); % get fft length
|
||||
% get data, pilot, and null carrier indices
|
||||
[dataIdx,pilotIdx] = helperSubcarrierIndices(cfgVHT,'VHT');
|
||||
dpIdx = [dataIdx; pilotIdx];
|
||||
nullIdx = 1:FFTLength;
|
||||
nullIdx(dpIdx) = [];
|
||||
|
||||
%% helper
|
||||
% anonymous function: sign extend and convert binary 14-bit-twocompl to int16
|
||||
twos2dec = @(x) typecast(uint16(bin2dec(x)),'int16');
|
||||
|
||||
%% read file
|
||||
p = readpcap();
|
||||
p.open([base_filename '.pcap']);
|
||||
%n = min(length(p.all()),100);
|
||||
n = p.length();
|
||||
p.from_start();
|
||||
|
||||
ts = zeros(n,1);
|
||||
% matrix to store calculated csi for each packet
|
||||
csi_buff = complex(zeros(n,FFTLength),0);
|
||||
k = 1; % target matrix counter
|
||||
% iterate over each packet
|
||||
while (k <= n)
|
||||
f = p.next();
|
||||
if isempty(f)
|
||||
disp('no more frames');
|
||||
break;
|
||||
end
|
||||
if f.header.orig_len ~= 1076
|
||||
continue;
|
||||
end
|
||||
ts(k) = double(f.header.ts_sec) + double(f.header.ts_usec) * 1e-6;
|
||||
payload = f.payload;
|
||||
|
||||
% convert to binary
|
||||
binary = dec2bin(payload,32);
|
||||
%disp(dec2hex(payload(14),8))
|
||||
% remove none-csi
|
||||
binary = binary(15:end,:);
|
||||
% extract imaginary and real parts
|
||||
real_b = binary(:,1:16);
|
||||
imag_b = binary(:,17:end);
|
||||
% group to cells
|
||||
real_b_cells = num2cell(real_b,2);
|
||||
imag_b_cells = num2cell(imag_b,2);
|
||||
% apply twos2dec for each cell
|
||||
real_d = cellfun(twos2dec,real_b_cells);
|
||||
imag_d = cellfun(twos2dec,imag_b_cells);
|
||||
% build complex numbers
|
||||
cmplx = complex(double(real_d), double(imag_d));
|
||||
|
||||
% throw away constant value at beginning
|
||||
% and extract used carriers
|
||||
if FFTLength <= 254
|
||||
% for 20 and 40 MHz
|
||||
cmplx_bw = fftshift(cmplx(2:FFTLength+1));
|
||||
else
|
||||
% exact format for 80 MHz currently unknown
|
||||
% only 255 values in CSI UDP, but FFTLength is 256
|
||||
cmplx_bw = fftshift([cmplx(1:FFTLength-1); 10000]);
|
||||
end
|
||||
|
||||
% zero set null carriers
|
||||
cmplx_bw(nullIdx) = 0.0;
|
||||
% store csi
|
||||
csi_buff(k,:) = cmplx_bw.';
|
||||
k = k + 1;
|
||||
end
|
||||
|
||||
%% save results
|
||||
if (should_save)
|
||||
save([base_filename '.mat'], 'csi_buff', '-v7.3');
|
||||
end
|
||||
|
||||
%% plot
|
||||
if (should_plot)
|
||||
% y-Axis ticks and ticklabels for phase
|
||||
ticky = [-180:45:180];
|
||||
tickyL = {'-180','','-90','','0°', '', '90°', '', '180°'};
|
||||
% x-Axis
|
||||
x = -FFTLength/2:FFTLength/2-1;
|
||||
|
||||
for n = 1:size(csi_buff,1)
|
||||
plot_chan = csi_buff(n,:);
|
||||
|
||||
figure(1);
|
||||
|
||||
% plot magnitude
|
||||
subplot(2,1,1)
|
||||
bha = bar(x,abs(plot_chan),'BarWidth',1);
|
||||
set(bha,'FaceColor',[0 0 1])
|
||||
set(bha,'EdgeColor',[0 0 0])
|
||||
title('CSI Magnitude')
|
||||
xlabel('Subcarrier Index')
|
||||
ylabel('Magnitude')
|
||||
grid on
|
||||
myAxis = axis();
|
||||
axis([min(x), max(x), myAxis(3), myAxis(4)])
|
||||
|
||||
% plot phase
|
||||
subplot(2,1,2)
|
||||
bha = bar(x,rad2deg(angle(plot_chan)),'BarWidth',1);
|
||||
set(bha,'FaceColor',[1 0 0])
|
||||
set(bha,'EdgeColor',[0 0 0])
|
||||
title('CSI Phase')
|
||||
xlabel('Subcarrier Index')
|
||||
ylabel('Phase in °')
|
||||
grid on
|
||||
set(gca,'YTick',ticky)
|
||||
set(gca,'YTickLabel',tickyL)
|
||||
myAxis = axis();
|
||||
axis([min(x), max(x), myAxis(3), myAxis(4)])
|
||||
|
||||
% wait for user input
|
||||
waitforbuttonpress();
|
||||
end
|
||||
|
||||
end
|
||||
|
||||
end
|
||||
|
|
@ -0,0 +1,181 @@
|
|||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
% %
|
||||
% ########### ########### ########## ########## %
|
||||
% ############ ############ ############ ############ %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ########### #### ###### ## ## ## ## ###### %
|
||||
% ########### #### # ## ## ## ## # # %
|
||||
% ## ## ###### ## ## ## ## # # %
|
||||
% ## ## # ## ## ## ## # # %
|
||||
% ############ ##### ###### ## ## ## ##### ###### %
|
||||
% ########### ########### ## ## ## ########## %
|
||||
% %
|
||||
% S E C U R E M O B I L E N E T W O R K I N G %
|
||||
% %
|
||||
% License: %
|
||||
% %
|
||||
% Copyright (c) 2018 Matthias Schulz %
|
||||
% %
|
||||
% Permission is hereby granted, free of charge, to any person obtaining a %
|
||||
% copy of this software and associated documentation files (the %
|
||||
% "Software"), to deal in the Software without restriction, including %
|
||||
% without limitation the rights to use, copy, modify, merge, publish, %
|
||||
% distribute, sublicense, and/or sell copies of the Software, and to %
|
||||
% permit persons to whom the Software is furnished to do so, subject to %
|
||||
% the following conditions: %
|
||||
% %
|
||||
% 1. The above copyright notice and this permission notice shall be %
|
||||
% include in all copies or substantial portions of the Software. %
|
||||
% %
|
||||
% 2. Any use of the Software which results in an academic publication or %
|
||||
% other publication which includes a bibliography must include %
|
||||
% citations to the nexmon project a) and the paper cited under b) or %
|
||||
% the thesis cited under c): %
|
||||
% %
|
||||
% a) "Matthias Schulz, Daniel Wegemer and Matthias Hollick. Nexmon: %
|
||||
% The C-based Firmware Patching Framework. https://nexmon.org" %
|
||||
% %
|
||||
% b) "Matthias Schulz, Jakob Link, Francesco Gringoli, and Matthias %
|
||||
% Hollick. Shadow Wi-Fi: Teaching Smartphones to Transmit Raw %
|
||||
% Signals and to Extract Channel State Information to Implement %
|
||||
% Practical Covert Channels over Wi-Fi. Accepted to appear in %
|
||||
% Proceedings of the 16th ACM International Conference on Mobile %
|
||||
% Systems, Applications, and Services (MobiSys 2018), June 2018." %
|
||||
% %
|
||||
% c) "Matthias Schulz. Teaching Your Wireless Card New Tricks: %
|
||||
% Smartphone Performance and Security Enhancements through Wi-Fi %
|
||||
% Firmware Modifications. Dr.-Ing. thesis, Technische Universität %
|
||||
% Darmstadt, Germany, February 2018." %
|
||||
% %
|
||||
% 3. The Software is not used by, in cooperation with, or on behalf of %
|
||||
% any armed forces, intelligence agencies, reconnaissance agencies, %
|
||||
% defense agencies, offense agencies or any supplier, contractor, or %
|
||||
% research associated. %
|
||||
% %
|
||||
% THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS %
|
||||
% OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF %
|
||||
% MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. %
|
||||
% IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY %
|
||||
% CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, %
|
||||
% TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE %
|
||||
% SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. %
|
||||
% %
|
||||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
|
||||
classdef readpcap < handle
|
||||
%READPCAP Summary of this class goes here
|
||||
% Detailed explanation goes here
|
||||
|
||||
properties
|
||||
fid;
|
||||
global_header;
|
||||
prev_len;
|
||||
end
|
||||
|
||||
methods
|
||||
function open(obj, filename)
|
||||
obj.fid = fopen(filename);
|
||||
|
||||
% should be 0xA1B2C3D4
|
||||
obj.global_header.magic_number = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% major version number
|
||||
obj.global_header.version_major = fread(obj.fid, 1, '*uint16');
|
||||
|
||||
% minor version number
|
||||
obj.global_header.version_minor = fread(obj.fid, 1, '*uint16');
|
||||
|
||||
% GMT to local correction
|
||||
obj.global_header.thiszone = fread(obj.fid, 1, '*int32');
|
||||
|
||||
% accuracy of timestamps
|
||||
obj.global_header.sigfigs = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% max length of captured packets, in octets
|
||||
obj.global_header.snaplen = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% data link type
|
||||
obj.global_header.network = fread(obj.fid, 1, '*uint32');
|
||||
end
|
||||
|
||||
function frame = next(obj)
|
||||
% timestamp seconds
|
||||
frame.header.ts_sec = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% timestamp microseconds
|
||||
frame.header.ts_usec = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% number of octets of packet saved in file
|
||||
frame.header.incl_len = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% actual length of packet
|
||||
frame.header.orig_len = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
if isempty(frame.header.incl_len)
|
||||
frame = [];
|
||||
return;
|
||||
end
|
||||
|
||||
% packet data
|
||||
if (mod(frame.header.incl_len,4)==0)
|
||||
frame.payload = fread(obj.fid, frame.header.incl_len/4, '*uint32');
|
||||
else
|
||||
frame.payload = fread(obj.fid, frame.header.incl_len, '*uint8');
|
||||
end
|
||||
end
|
||||
|
||||
function frame = next_header(obj)
|
||||
% timestamp seconds
|
||||
frame.header.ts_sec = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% timestamp microseconds
|
||||
frame.header.ts_usec = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% number of octets of packet saved in file
|
||||
frame.header.incl_len = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
% actual length of packet
|
||||
frame.header.orig_len = fread(obj.fid, 1, '*uint32');
|
||||
|
||||
if isempty(frame.header.incl_len)
|
||||
frame = [];
|
||||
return;
|
||||
end
|
||||
|
||||
fseek(obj.fid, frame.header.incl_len, 0);
|
||||
end
|
||||
|
||||
function from_start(obj)
|
||||
fseek(obj.fid, 24, -1);
|
||||
end
|
||||
|
||||
function frames = all(obj)
|
||||
i = 1;
|
||||
frames = cell(1);
|
||||
obj.from_start();
|
||||
while true
|
||||
frame = obj.next();
|
||||
|
||||
if isempty(frame)
|
||||
break;
|
||||
end
|
||||
|
||||
frames{i} = frame;
|
||||
i = i + 1;
|
||||
end
|
||||
end
|
||||
|
||||
function len = length(obj)
|
||||
len = 0;
|
||||
obj.from_start();
|
||||
f = obj.next_header();
|
||||
while ~isempty(f)
|
||||
len = len + 1;
|
||||
f = obj.next_header();
|
||||
end
|
||||
end
|
||||
end
|
||||
|
||||
end
|
||||
|
||||
Binary file not shown.
|
After Width: | Height: | Size: 507 KiB |
|
|
@ -0,0 +1,69 @@
|
|||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
% %
|
||||
% ########### ########### ########## ########## %
|
||||
% ############ ############ ############ ############ %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ## ## ## ## ## ## ## %
|
||||
% ########### #### ###### ## ## ## ## ###### %
|
||||
% ########### #### # ## ## ## ## # # %
|
||||
% ## ## ###### ## ## ## ## # # %
|
||||
% ## ## # ## ## ## ## # # %
|
||||
% ############ ##### ###### ## ## ## ##### ###### %
|
||||
% ########### ########### ## ## ## ########## %
|
||||
% %
|
||||
% S E C U R E M O B I L E N E T W O R K I N G %
|
||||
% %
|
||||
% License: %
|
||||
% %
|
||||
% Copyright (c) 2018 Jakob Link, Matthias Schulz %
|
||||
% %
|
||||
% Permission is hereby granted, free of charge, to any person obtaining a %
|
||||
% copy of this software and associated documentation files (the %
|
||||
% "Software"), to deal in the Software without restriction, including %
|
||||
% without limitation the rights to use, copy, modify, merge, publish, %
|
||||
% distribute, sublicense, and/or sell copies of the Software, and to %
|
||||
% permit persons to whom the Software is furnished to do so, subject to %
|
||||
% the following conditions: %
|
||||
% %
|
||||
% 1. The above copyright notice and this permission notice shall be %
|
||||
% include in all copies or substantial portions of the Software. %
|
||||
% %
|
||||
% 2. Any use of the Software which results in an academic publication or %
|
||||
% other publication which includes a bibliography must include %
|
||||
% citations to the nexmon project a) and the paper cited under b) or %
|
||||
% the thesis cited under c): %
|
||||
% %
|
||||
% a) "Matthias Schulz, Daniel Wegemer and Matthias Hollick. Nexmon: %
|
||||
% The C-based Firmware Patching Framework. https://nexmon.org" %
|
||||
% %
|
||||
% b) "Matthias Schulz, Jakob Link, Francesco Gringoli, and Matthias %
|
||||
% Hollick. Shadow Wi-Fi: Teaching Smartphones to Transmit Raw %
|
||||
% Signals and to Extract Channel State Information to Implement %
|
||||
% Practical Covert Channels over Wi-Fi. Accepted to appear in %
|
||||
% Proceedings of the 16th ACM International Conference on Mobile %
|
||||
% Systems, Applications, and Services (MobiSys 2018), June 2018." %
|
||||
% %
|
||||
% c) "Matthias Schulz. Teaching Your Wireless Card New Tricks: %
|
||||
% Smartphone Performance and Security Enhancements through Wi-Fi %
|
||||
% Firmware Modifications. Dr.-Ing. thesis, Technische Universität %
|
||||
% Darmstadt, Germany, February 2018." %
|
||||
% %
|
||||
% 3. The Software is not used by, in cooperation with, or on behalf of %
|
||||
% any armed forces, intelligence agencies, reconnaissance agencies, %
|
||||
% defense agencies, offense agencies or any supplier, contractor, or %
|
||||
% research associated. %
|
||||
% %
|
||||
% THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS %
|
||||
% OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF %
|
||||
% MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. %
|
||||
% IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY %
|
||||
% CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, %
|
||||
% TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE %
|
||||
% SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. %
|
||||
% %
|
||||
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
|
||||
|
||||
disp('Reading PCAP files - this takes a while ...');
|
||||
csi_buff_microwave = readcsi('experiment2c_microwave', 0, 0);
|
||||
csi_buff_outside = readcsi('experiment2c_outside', 0, 0);
|
||||
csi_plot(csi_buff_microwave, csi_buff_outside);
|
||||
Loading…
Reference in New Issue